Automating Cloud Infrastructure – Project
During my two-month internship at Linprofs, I embarked on an exciting project that involved automating cloud infrastructure using Terraform and Ansible. As part of my final year in higher education, this project was a significant learning experience that allowed me to delve deep into Infrastructure as Code (IaC) and configuration management. In this blog post, I’ll walk you through the steps I took to complete this project, detailing the process from creating the initial infrastructure to securing and managing it with Ansible playbooks, and finally, conducting a vulnerability assessment with Nessus.
Setting Up the Control Node
The journey began with setting up a control node, which is the machine from where I executed all my Terraform and Ansible commands. This node was equipped with the necessary tools: Terraform, Ansible, and Nessus. Installing these tools was straightforward, thanks to the comprehensive documentation available.
Defining the Infrastructure with Terraform
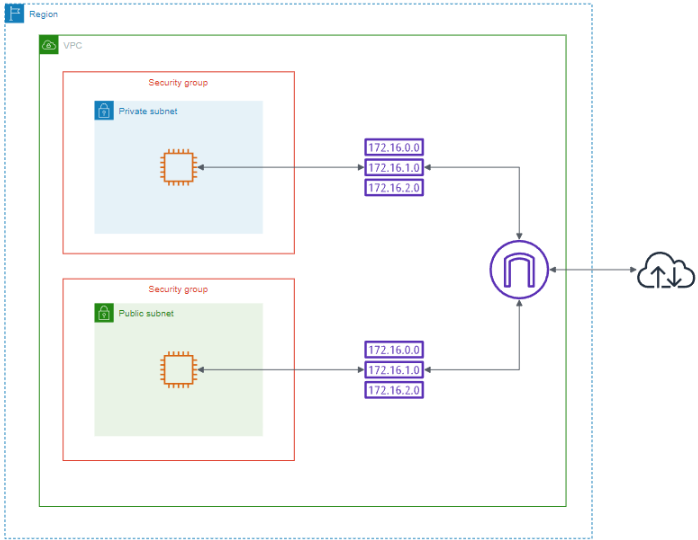
Next, I defined the infrastructure using Terraform. The goal was to create a Virtual Private Cloud (VPC) in AWS that included:
- Two subnets: one private and one public.
- Each subnet having its own security group.
- Two routing tables.
- An internet gateway to enable traffic to the internet.
Deploying the Infrastructure
With the infrastructure defined, I deployed it using Terraform. The deployment process was seamless, and within minutes, the VPC, subnets, security groups, EC2 instances, and internet gateway were up and running. The infrastructure setup is visually represented in the following diagram:
Configuring the Environment with Ansible
Once the infrastructure was in place, the next step was to configure it using Ansible playbooks. The tasks included:
- Updating the managed nodes.
- Creating groups and users.
- Installing the Apache web service on the public EC2 instance.
- Updating the SSH configuration file for enhanced security.
Scanning for Vulnerabilities with Nessus
After configuring the environment, I used Nessus to scan for vulnerabilities. This step was crucial to ensure that the infrastructure was secure and complied with best practices. Nessus provided a detailed report highlighting the areas that needed attention.
Addressing Vulnerabilities
Based on the Nessus report, I made the necessary updates to the Ansible playbooks and the control node to address any identified vulnerabilities. This iterative process of scanning and updating ensured a robust and secure infrastructure.
This project was a great learning opportunity, allowing me to gain hands-on experience with Terraform and Ansible. Automating the cloud infrastructure not only streamlined the deployment process but also ensured consistent and secure configurations. My internship at Linprofs provided a solid foundation in IaC and configuration management, skills that are invaluable in today’s cloud-driven world.
Explore more about our interns’ assignments and their impactful contributions. Click here to learn more!



Comments are closed