Do you know what ransomware is? If you don’t, don’t worry; you are not alone in being unfamiliar with it and that’s why we decided to write this article because we believe it is crucial for people to educate themselves and be conscious of this threat.
Last year, after we participated at an event in Spain, where we attended a talk about ransomware, we realized how important it is for everyone to know more about this threat and understand it.
Defending Against the Rise of Ransomware Attacks: Strategies, Prevention, and Recovery
In today’s digitally interconnected world, the specter of ransomware looms large over individuals, businesses, and institutions alike. With each passing day, cybercriminals are devising more sophisticated methods to infiltrate systems, encrypt valuable data, and demand hefty ransoms for its release. Understanding the nuances of this pervasive threat is paramount in fortifying defenses and safeguarding against potentially devastating consequences.
Even if the official numbers of companies demanding ransoms are quite high, it’s important to note that there are likely many more attacks that go unreported. Most companies opt not to disclose such incidents to their clients, either to maintain their reputation or due to embarrassment over their lack of preparedness. This reluctance to acknowledge breaches underscores the need for greater transparency and proactive measures to combat ransomware threats effectively.
How do drives get infected with Ransomware
Ransomware is a type of malware that encrypts files or blocks access to systems, holding them hostage until a ransom is paid. This threat has become increasingly common, with attackers targeting industries like healthcare, finance, government, and education.
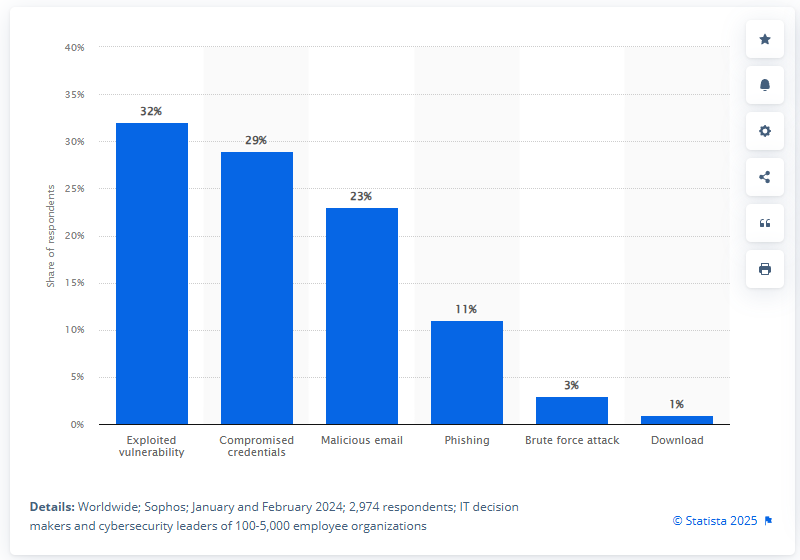
How does ransomware spread through a network? These attacks typically start through phishing emails, compromised websites, or weaknesses in remote desktop protocols (RDPs). Once inside a network, ransomware spreads quickly, using advanced encryption to lock files. Cybercriminals then demand payment to unlock the data, leaving organizations grappling with significant disruptions.
The High Stakes of Ransom Payments
While victims may feel compelled to pay the ransom to regain control of their data, doing so is fraught with risks. Not only does it embolden cybercriminals to continue their nefarious activities, but there’s also no guarantee that paying the ransom will result in data recovery. Moreover, succumbing to extortion can attract further targeting by hackers.
Building Resilience: Strategies for Protection
Prevention is key to mitigating the impact of ransomware attacks. While cyber insurance offers financial protection by covering costs such as investigations, ransom payments, and business interruptions, it is not a substitute for robust cybersecurity measures. Cyber attackers may even target insurance documents to determine the ransom they demand.
Strong prevention strategies include maintaining secure backups, providing employee training, using up-to-date antivirus software, and promptly patching security vulnerabilities to strengthen defenses against emerging threats.
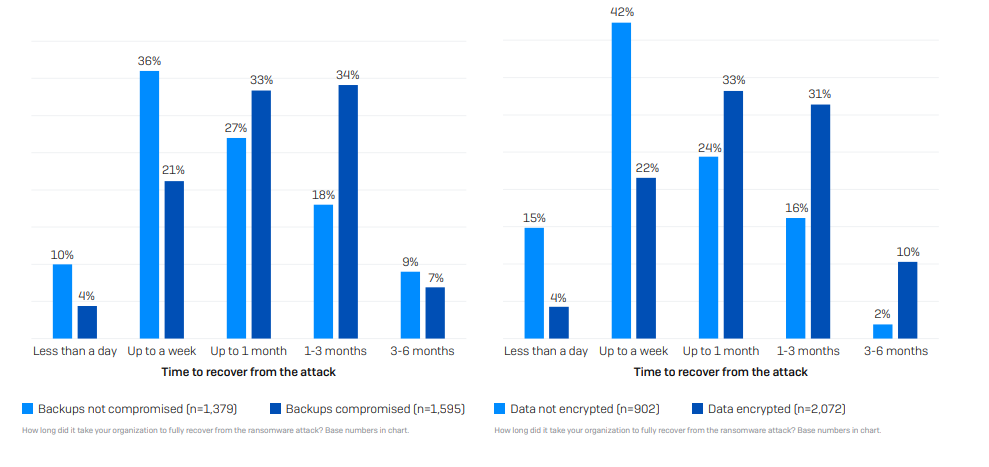
However, even with the best defenses, ransomware attacks can still occur. A well-defined incident response plan is essential, including isolating infected systems, notifying authorities, engaging cybersecurity experts, and leveraging secure backups to minimize downtime and financial losses.
Collaboration among stakeholders—government agencies, law enforcement, private organizations, and cybersecurity professionals—is crucial in combatting ransomware. Sharing threat intelligence, developing proactive strategies, and prosecuting attackers collectively build a resilient defense against this persistent threat.
Ransomware poses a formidable challenge to the integrity and security of digital infrastructure worldwide. As cyber threats evolve, vigilance and preparedness are paramount. By understanding the tactics employed by cybercriminals, implementing robust security measures, and fostering collaboration within the cybersecurity community, organizations can fortify their defenses and mitigate the impact of ransomware attacks. Together, we can thwart the advances of malicious actors and safeguard the digital realm for generations to come.
Explore more malware threats and stay informed by visiting our cybersecurity category for in-depth insights and tips to protect yourself and your organization.



Comments are closed