What is a Trojan Horse Virus?
Trojan is a type of malicious software that disguises itself as legitimate software to trick users into installing it. Once inside a system, Trojans can steal sensitive information, create backdoors, or install additional malware.
Common Signs of a Trojan Infection
Recognizing the early signs of a Trojan infection can prevent further damage. One of the most noticeable symptoms is a significant slowdown in system performance. Your computer may lag, freeze, or crash unexpectedly due to excessive CPU and RAM usage caused by the malware.
Another common sign is the presence of unusual pop-ups and browser redirects. If you notice frequent, unexpected advertisements or find yourself redirected to suspicious websites, a Trojan might be operating in the background.
You may also discover unknown applications or files on your device. If you find software installed that you don’t remember downloading, it could be a Trojan attempting to blend in with legitimate programs.
High internet activity is another red flag. If your network usage spikes without any known reason, it may indicate that malware is communicating with a remote server. Additionally, some Trojans attempt to disable antivirus or security software to avoid detection, leaving your system unprotected.
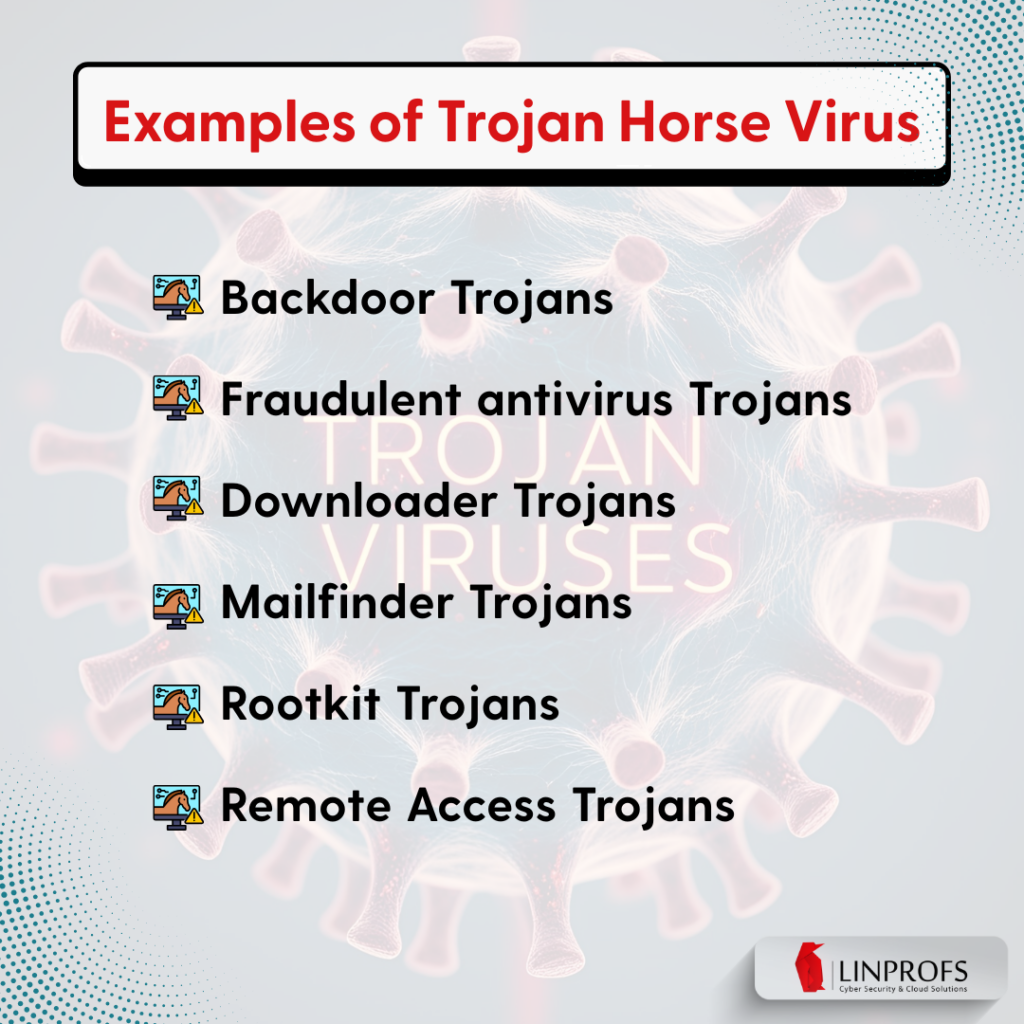
How do Cybercriminals use Trojans?
Cybercriminals use it in various ways to compromise systems and exploit users. One of the primary methods is data theft, where the malware steals personal, financial, or business information for illicit purposes.
Another dangerous use is remote access. Some Trojans create backdoors that allow hackers to control an infected system remotely. This unauthorized access can lead to serious consequences, including further malware installation or data manipulation.
These viruses are also used to integrate infected devices into botnets, which are networks of compromised computers controlled by cybercriminals. These botnets are often deployed for large-scale cyberattacks, such as Distributed Denial-of-Service (DDoS) attacks.
Additionally, Trojans can serve as a delivery mechanism for other types of malware, such as ransomware, spyware, or keyloggers. By installing additional malicious software, a single Trojan infection can escalate into a much larger security threat.
Best Tools to Remove Trojan Viruses
If you suspect a infection on your system, using reliable security tools is essential for detection and removal. Malwarebytes is a widely recognized tool that effectively detects and eliminates Trojans. Windows Defender, the built-in protection for Windows users, also provides a solid defense against malware threats.
Bitdefender is another powerful antivirus program that offers advanced scanning and real-time protection against Trojans. Avast Free Antivirus is a user-friendly option that provides free malware detection, making it accessible for users on a budget. Kaspersky Anti-Virus is also a comprehensive security solution known for its strong malware detection capabilities.
To eliminate it from a Linux system, you can use security tools like ClamAV, chkrootkit, rkhunter, and Lynis to detect and remove malware. ClamAV scans for viruses, while chkrootkit and rkhunter focus on rootkits and backdoors. Maldetect (LMD) is particularly useful for web servers. Keeping your system updated, removing suspicious files, and monitoring network activity can further enhance security. If an infection persists, consider restoring from a clean backup.
How to Protect Your System
Preventing a Trojan infection is crucial for maintaining a secure system. One of the best practices is to avoid downloading unknown files. Be cautious with email attachments and software downloads, as cybercriminals often use deceptive tactics to distribute malware.
Keeping your operating system and software updated is another key step. Regular updates patch vulnerabilities that hackers may exploit to install Trojans on your system.
Using a strong antivirus program is highly recommended. Real-time protection ensures that potential threats are detected before they can cause harm. Additionally, enabling a firewall adds an extra layer of defense by blocking unauthorized access attempts.
Staying alert to phishing scams is also important. Cybercriminals often use emails and fake websites to trick users into downloading Trojan-infected files. Always verify the legitimacy of links and attachments before clicking on them.
Trojans are among the most deceptive and dangerous types of malware. Detecting early signs of infection, using reliable security tools, and following best practices can help you stay protected. Staying vigilant and prioritizing cybersecurity measures is essential in safeguarding your data and devices from these persistent threats.
Explore more malware threats and stay informed by visiting our cybersecurity category for in-depth insights and tips to protect yourself and your organization.



Comments are closed