What Are Computer Worms and how they work?
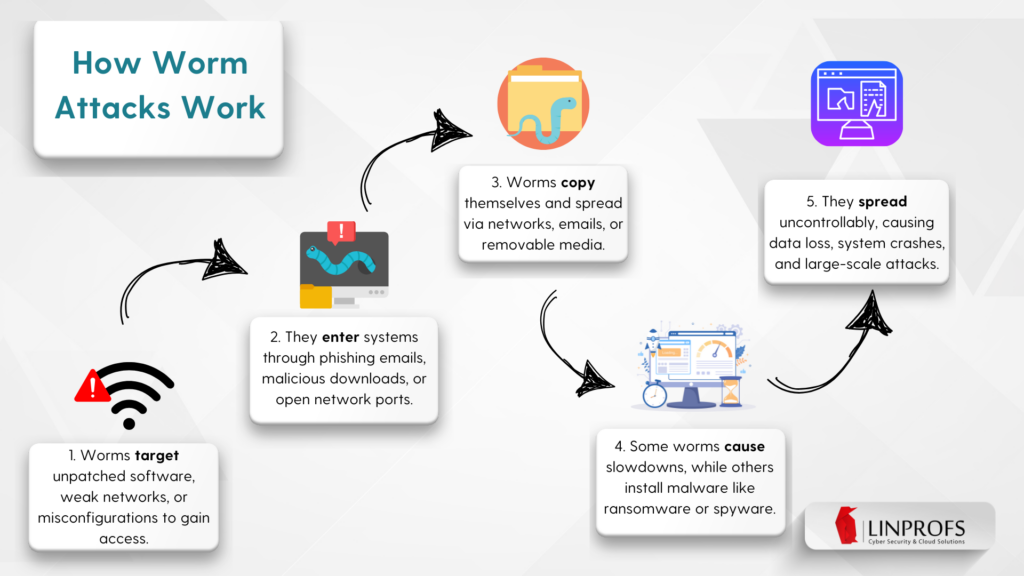
A computer worm is a type of malware that can spread independently across networks and devices without requiring human interaction. Unlike viruses, which need a host file to attach to, worms exploit security vulnerabilities to replicate themselves and spread. These malicious programs can cause extensive damage, from slowing down networks to stealing sensitive information.
Worms typically spread by exploiting software vulnerabilities, weak passwords, or social engineering tactics. Once inside a system, they can consume bandwidth and system resources, leading to network slowdowns. They may also install additional malware like spyware or ransomware, create backdoors for cybercriminals to gain unauthorized access, and steal sensitive data such as login credentials and financial information. Additionally, worms can disable security defenses, making systems more susceptible to further attacks.
Well-Known Worm Incidents Over The years
Some of the most infamous worms in history include:
Morris Worm (1988): One of the first worms, it slowed down early internet systems and showcased the dangers of self-replicating malware.
ILOVEYOU (2000): Spread via email attachments, tricking users into opening a file that led to widespread system corruption and financial losses.
Code Red (2001): Targeted Microsoft IIS servers, defacing websites and launching denial-of-service (DoS) attacks.
Blaster (2003): Exploited Windows vulnerabilities to spread rapidly, forcing widespread system reboots and disruptions.
Conficker (2008): Created botnets to take control of infected machines, highlighting the risks of unpatched software.
WannaCry (2017): A ransomware worm that exploited Windows vulnerabilities, encrypting user data and demanding payments in cryptocurrency.
EternalBlue-Based Worms (2017-Present) – Variants like NotPetya and Bad Rabbit leveraged the same vulnerability to spread rapidly, affecting critical infrastructure worldwide.
How to protect against this worm malware?
To defend against computer worm malware, organizations and individuals should take proactive security measures, including:
Keeping software, applications, and operating systems updated to patch vulnerabilities.
Using strong passwords and enabling multi-factor authentication (MFA) to prevent unauthorized access.
Installing reliable antivirus and endpoint protection solutions that detect and remove malware.
Avoiding suspicious emails, links, and attachments that could contain malicious code.
Implementing network segmentation and firewalls to limit the spread of worms within a system.
Regularly backing up critical data to minimize the impact of a potential infection.
Educating employees and users about cybersecurity best practices to reduce the risk of social engineering attacks.
Computer worm malware remains a serious cybersecurity threat, continuously evolving with new techniques to infiltrate systems and exploit weaknesses. Unlike other types of malware, worms require no user interaction to spread, making them particularly dangerous. Staying informed and implementing robust security measures can help mitigate the risks associated with these self-propagating threats. By taking proactive steps, individuals and organizations can protect their networks and ensure their data remains secure in an increasingly digital world.
Expand your knowledge on cybersecurity. Explore different types of malware and learn how to protect yourself by choosing the malware category.



Comments are closed